As a former analyst (I spent 6 years as Research VP at Forrester), I have been asked many times “what makes a good analyst presentation?”
Throughout my time at Forrester, I saw countless vendor presentations; some great, some mediocre, others were a downright waste of time. As I began reflecting on all the presentations and demos that I sat through, it became apparent that how few marketers actually know the art of making an impactful, concise presentation that leaves a long-lasting impression.
Years ago, I took a briefing from Google Apps team when they released Google App Engine. The entire presentation had 10 slides. We finished it within 30 minutes; I understood precisely what they were trying to say; they said it with finesse, and it rocked my world. Early last year, I had the good fortune of being briefed by Sonatype. The team over there brought a visually compelling deck with precisely-crafted messaging and highly organized content; it was another memorable experience. Other notable encounters included those with Kony Solutions, MobileIron, and Dome9.
What do all these presentations have in common?
They are all concise, to the point, with a central message to drive. With little superfluous information, and good support evidence to boot, they were all fashioned by the hands of an experienced marketer who was also an excellent communicator.
A good communicator can get points across and leave a powerful impression with a minimum amount of content. My thesis is that anyone can do a good presentation in eight slides, as long as you focus on this structure,
- What is the problem & why is it interesting? (1 or 2 slides)
- How do you solve the problem? ( 3 slides)
- Why are you uniquely qualified to solve the problem? (1 slide)
- Interesting customer deployments (1 slide)
- Forward looking roadmap (1 slide)
- Takeaways (1 slide)
1. What is the problem you are solving and why is it interesting?
If you can’t explain the problem in one or two slides, perhaps the problem is not that compelling. A common mistake of marketers is overhyping the problem. Trust me, a good analyst knows the problem space—you don’t need to pile on statistics and market trends to convince him/her.
On this slide, you need to articulate the problem, indicate the scope, and get the analyst interested. Tall order, you bet it is, but it can be done. Shown below was Google’s opening slide that teed up the motivation for Google App Engine.

Figure 1: Google’s first slide motivating the problemm.
There is very little text on this slide, but it includes everything that needs to be said. The slide conveyed that there are many development paradigms, languages, and platforms, which can lead to complex application development tasks.
Sonatype used two slides to motivate and frame the problem.
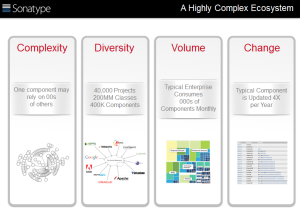

Both slides have well organized content, visually interesting, and a focused message.
At this point, the analyst should know what the problem is that you are trying to tackle and her interest, hopefully, is heightened because of the way you described the problem. Now, onto the next step…
2. How do you solve the problem?
This is of course the meat of the presentation. In this section, you should cover these basics:
- You value proposition
- Description of your technology
- Ways to operationalize your product
Google put up one slide on App Engine, what it is (Python and Java run-times), what it includes (Servlet and APIs), and some sample applications (cron jobs and DB I/O). (see below)
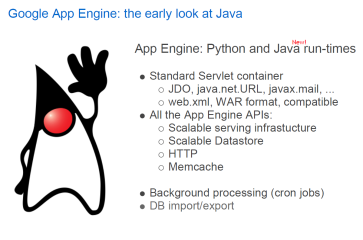
Google also had another slide on Secure Data Connector to show how you would access data behind the firewall. Google was light on value proposition, but we got that through discussions.
Sonatype’s three slides mirrored the three basic points perfectly. First was the value proposition slide.

And there was the system description.
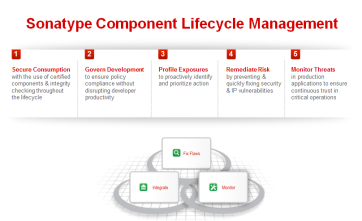
Finally the operational picture.
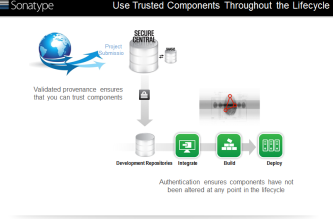
It’s extremely important to keep in mind, as you develop content for this section, that your aim should be to describe how the product help solve customer’s problem, not how awesome the product is. There is a subtle but important difference here.
Anton Chuvakin from Gartner, a friend of mine, has always had a beef on this issue and said multiple times that how few people understand the difference between the two. But once you do, and know how to leverage it, your presentation and demo will be on a different level.
Be prepared to engage in an active discussion in this part of the presentation. Encourage the analyst to ask as many questions as he/she cares to.
3. Why are you uniquely qualified to solve the problem?
This one is a bit tricky. Here you need to highlight your strength – what you are doing that your competitors are not doing or not capable of doing. This is often the most contentious of the discussion topics. Your best bet is to focus on your strength, rather than the competitor’s weaknesses. If the analyst is any good, he or she will be naturally suspicious if you talk down your competitor too much.
A few things to keep in mind when you articulate your competitive strength:
– Be proud of your technology: Does it show, in the text, in the way content flows, and in the way you talk, that you are proud of what you will present? Do you believe in the technology? You need to believe to be proud. Being proud is infectious and it will set a tone for the presentation.
– Focus on your strength, not other’s weaknesses: It is the analyst’s job to compare you against your competition. Your job is to ensure that the analyst is well informed of your strength.
– Articulate your value with facts, not claims: Statements such as: “Because we already have function A and function B, we are in a good position to provide deep integration from these two vantage points” will be well received. In contrast, statements like “no one else can do this because we are the number one vendor in the market” will go over poorly.
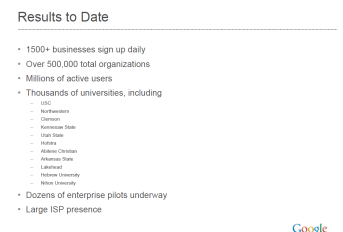
The slide below is how Google articulated why they are uniquely qualified to solve the problem – with 1500 businesses signing up to Google Apps, more than half a million corporate accounts, and millions of active users. These are indeed powerful statistics.
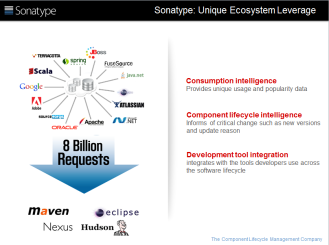
And below is how Sonatype communicated why they are uniquely positioned. They handle 8 million component requests a day, with an extensive coverage of open source component usage, popularity, and development tool integration.
4. Interesting customer deployments
I cannot stress enough how important it is to have customer examples/testimonials as part of your content. In fact, you should not go in front of an analyst unless you have good customer deployment examples to discuss. They do not have to be named customers, but it’s highly desirable to show an interesting customer use case (or two) to ground the discussion. I would
be even more interesting if you can show a customer deployment scenario with uncommon challenges, e.g., scale, complexity, or problem nature, that you technology helped to tackle.
This was Google’s customer adoption slide.

Followed by another example,
Sonatype did it slightly differently. On each slide that explained their technology, they included a user quote at the bottom. On the slide depicting IDE integration, the quote says: “I can quickly pick the best component from the start, eliminating downstream work”. On the slide discussing real time component selection, the quote says: “Our research time has been reduced significantly with the component suggestion info”
Customer’s words, not yours. Plain and simple.
5. Forward-looking roadmap
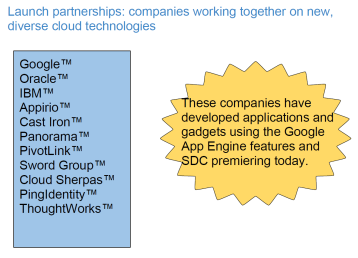
This maybe optional for some presentations, but it’s always fun to show where you’d go next. Google summed it up in one simple slide – launching partnerships.
6. Takeaways
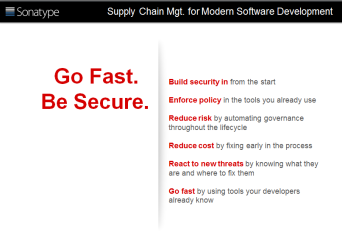
Think about what you want the analyst to remember, even if she doesn’t remember anything else from the presentation. Focus on that as your take-way slide. Sonatype did a nice job of exactly that; the final slide was simple, direct, and impactful. Nearly a year later, I still remember the “Go fast, be secure” tag line.
So there you have it – the secret to making a good analyst presentation.
Before I end this blog post, it bears repeating a few “Do’s” and “Don’ts” in analyst communication.
Do’s
- Think low entropy. Focus on what you want to say and articulate that. Do not overwhelm the presentation with unnecessary or secondary information. Remember, you only have 30 minutes or 1 hour with the analyst, edit yourself and make it count.
- Be visual: Usually when the analyst takes a vendor briefing, she is on the phone staring into a computer monitor. Please, give her something visual to keep her interested.
- Show how you solve problems, not how you use the product: The analyst can care less about how one might use your product, if the product is not interesting or the value proposition is not compelling. Frame your discussion in the context of solving customer’s problems is the only way to keep a bleary-eyed analyst engaged throughout the discussion.
- Research the analyst: Read their reports ahead of time. Understand the point of view of the analyst. Understand how she defines the market and talk to that angle. Remove quotes form Gartner if you are talking to Forrester, and vice versa.
- Stress test your presentation: You only get to make the first impression once. Before you get in front of the analyst, put the presentation in front of your customers, run it through your partners, and get them to critique it.
Don’ts
- Don’t start with a solution and look for a problem: Too often we get briefings that are clearly solutions looking for problems. A good analyst who sat through many presentations can see through that quickly and will lose interest before you can say “next slide”. Again, if it takes a while to explain why you work on this problem, the problem ain’t worth it.
- Don’t dwell on your competitors: Focus on your solution and your strength. Unless the analyst asks, do not spend time discussing your competitors. Describing what your competitor can and cannot do is a minefield of a topic that is best avoided.
- Don’t jam your slide with text: There is nothing worse than sitting in front of webex and seeing it load a slide that looks like this one below. (This was from an actual vendor presentation, the names of which have been removed). And please, under no circumstances should you read word after word from the slide. That is the single biggest offense you can commit for a remote presentation – a sure way of putting your audience to sleep.

- Don’t treat the analyst as an extension of your marketing department: Remember that the analyst does not work for your company; they do not have to care what you have to say. It is your job to get them intrigued and interested. Your goal should not be to get them to write about you (if you start with this goal, you will most likely fail). Your goal, instead, is to get them interested in what you have to say. As long as there is interest, there will be possibilities.















